Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
Por um escritor misterioso
Descrição
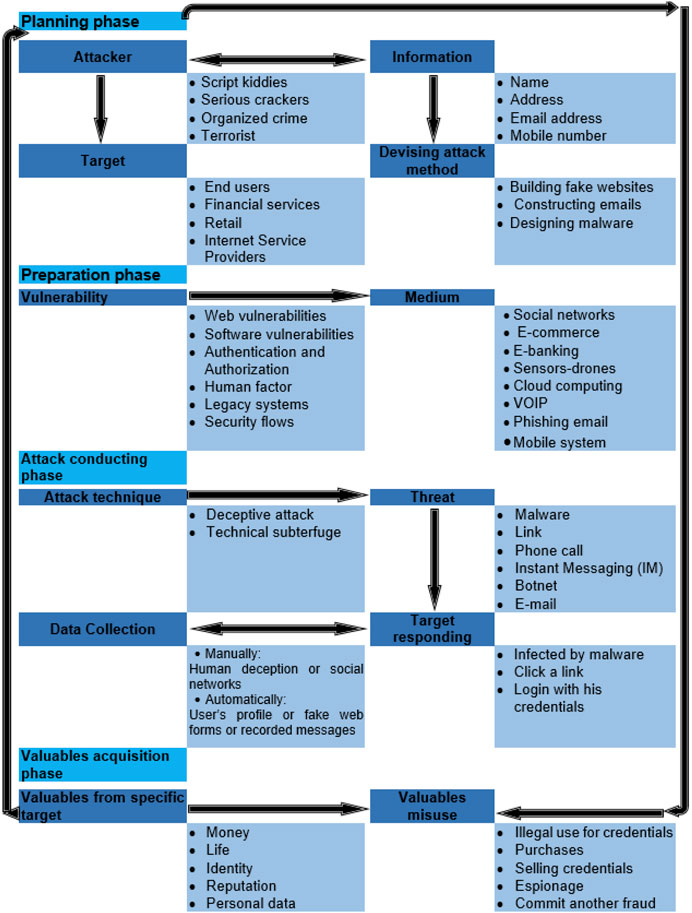
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy

Technical Reviews Sumitomo Electric

PDF] Signature-Based Malware Detection Using Approximate Boyer Moore String Matching Algorithm

Cycle‐Consistent Generative Adversarial Network and Crypto Hash Signature Token‐based Block chain Technology for Data Aggregation with Secured Routing in Wireless Sensor Networks - Janarthanan - International Journal of Communication Systems - Wiley

A Comprehensive Survey of Recent Internet Measurement Techniques for Cyber Security - ScienceDirect

Sensors, Free Full-Text
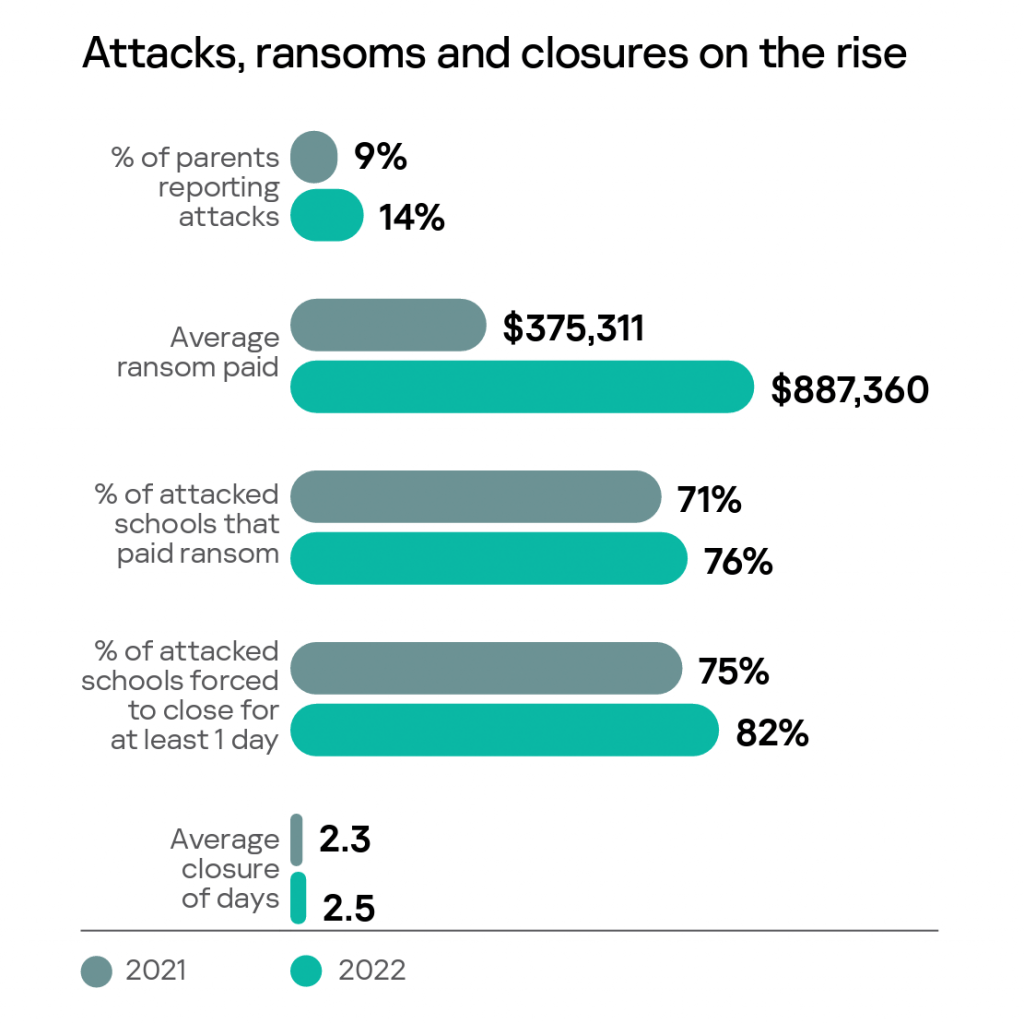
CTO/CIO Archives • TechNotes Blog
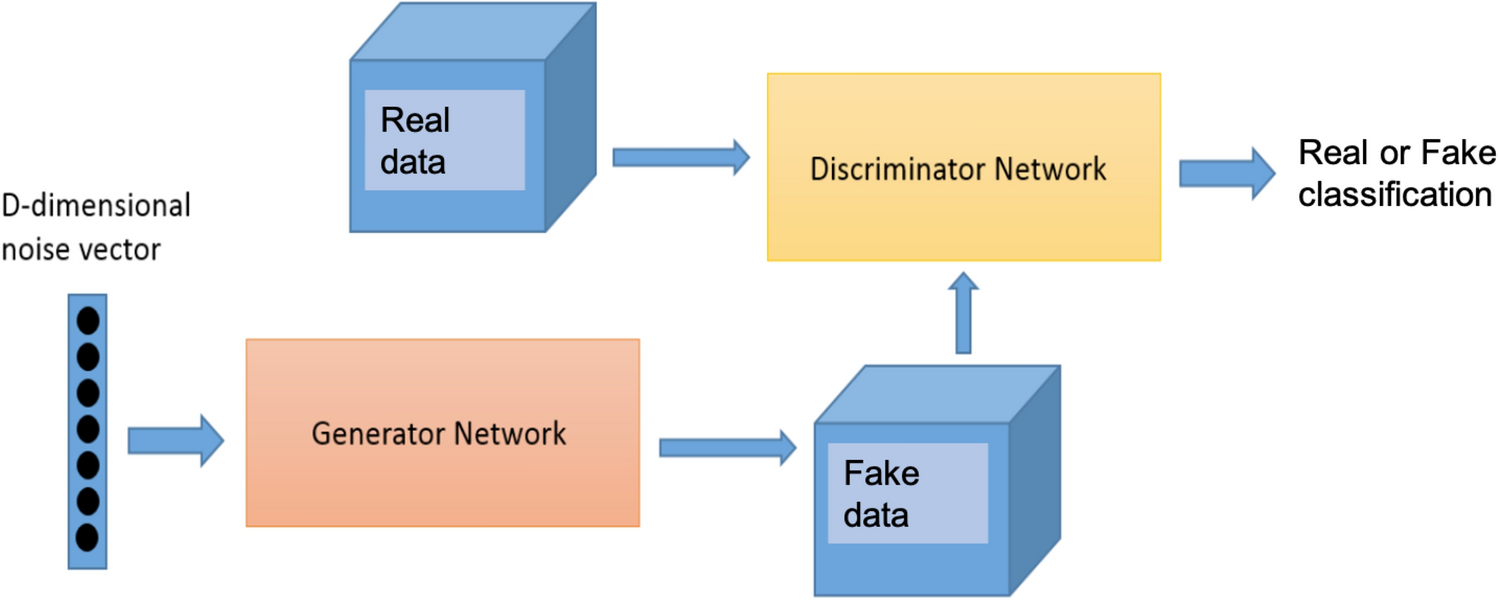
Synthetic flow-based cryptomining attack generation through Generative Adversarial Networks

Deep Learning for Zero-day Malware Detection and Classification: A Survey
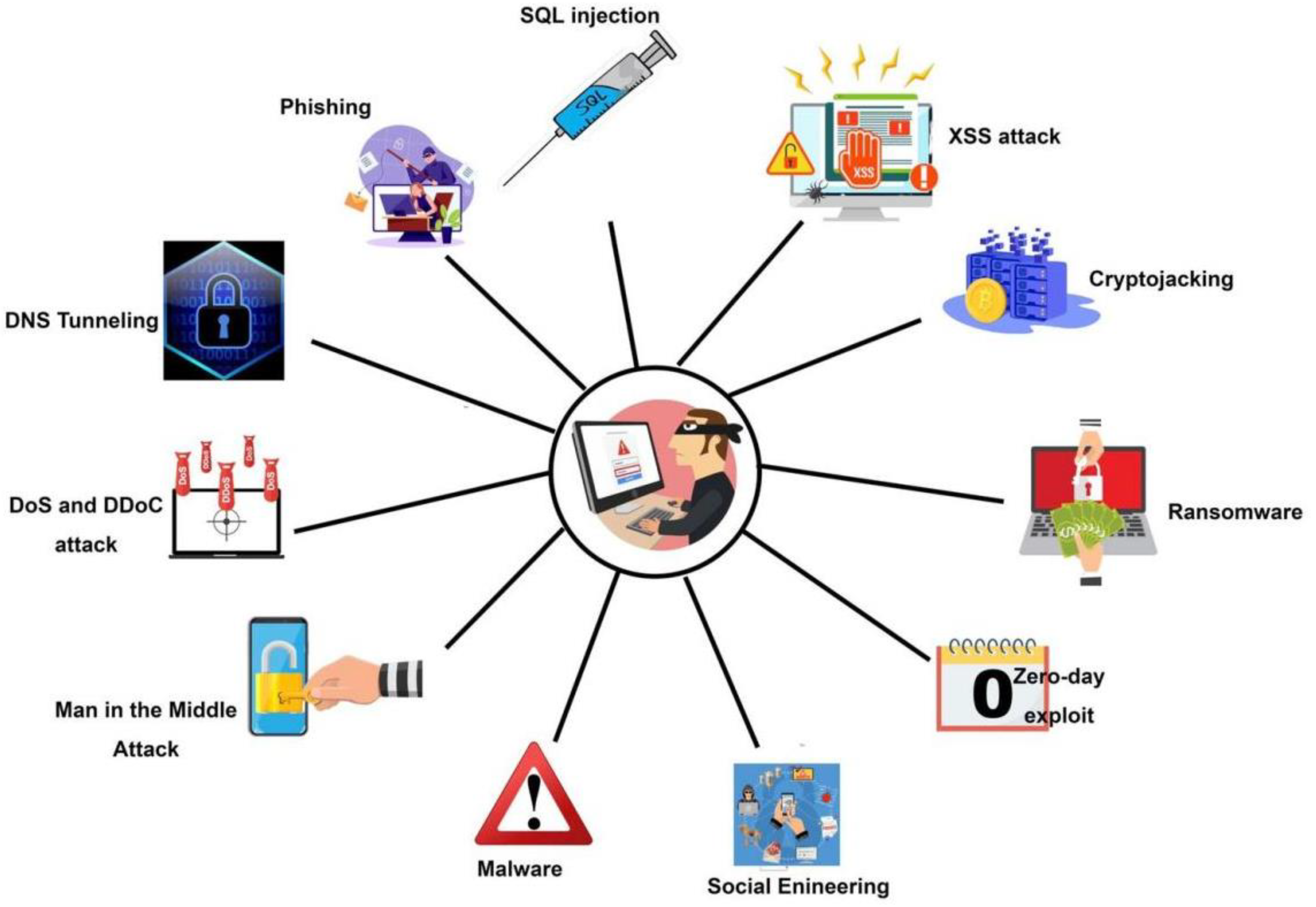
Symmetry, Free Full-Text
de
por adulto (o preço varia de acordo com o tamanho do grupo)