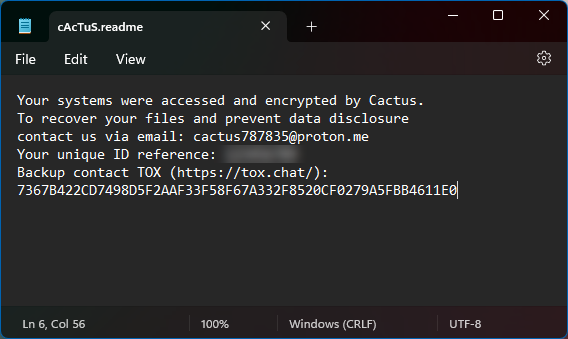
CACTUS ransomware evades antivirus and exploits VPN flaws to hack networks
Por um escritor misterioso
Descrição
CACTUS ransomware operators target large-scale commercial organizations with double extortion to steal sensitive data before encryption.

Antivirus and Ransomware - Cyber Security Informer

Power Rankings: Ransomware Malicious Quartile Q3 2023

May 2023: Recent Cyber Attacks, Data Breaches & Ransomware Attacks

2020 Cyber Attacks Statistics – HACKMAGEDDON
Microsoft Alerts of New Cactus Ransomware Attacks – Gridinsoft

New Ransomware Strain 'CACTUS' Exploits VPN Flaws to Infiltrate Networks
the revolutionary
The Latest Version of the Big Head Ransomware Unveils a Bogus Windows Update Alert

Cactus Ransomware Infiltrates Networks by Exploiting VPN Flaws

Developments in the ransomware underworld: ALPHV, Akira, Cactus, and Royal. Some organizations remain vulnerable to problems with unpatched Go-Anywhere instances.

1-15 May 2023 Cyber Attacks Timeline – HACKMAGEDDON
New Cactus ransomware encrypts itself to evade antivirus

Cactus Ransomware Exploiting Qlik code execution Vulnerability
de
por adulto (o preço varia de acordo com o tamanho do grupo)