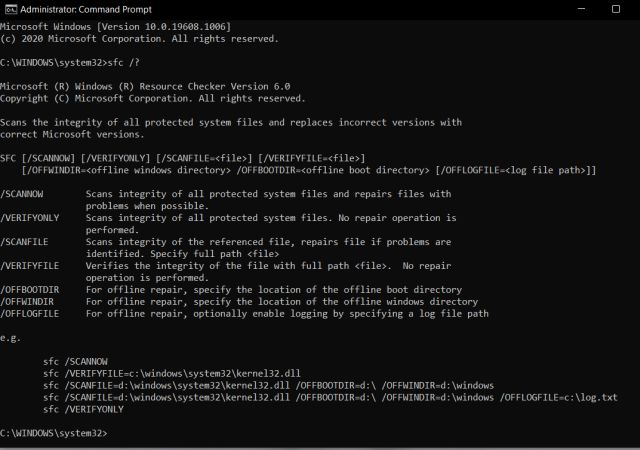
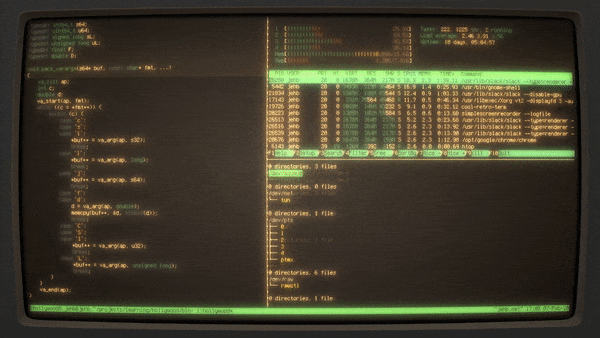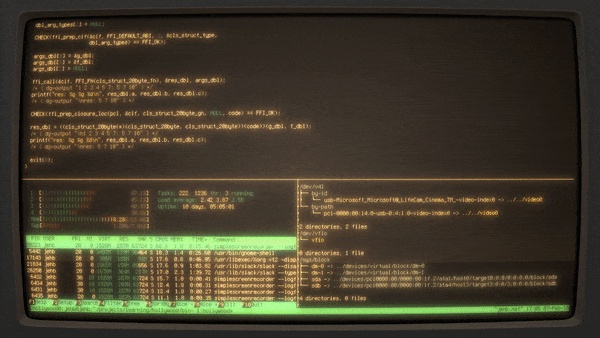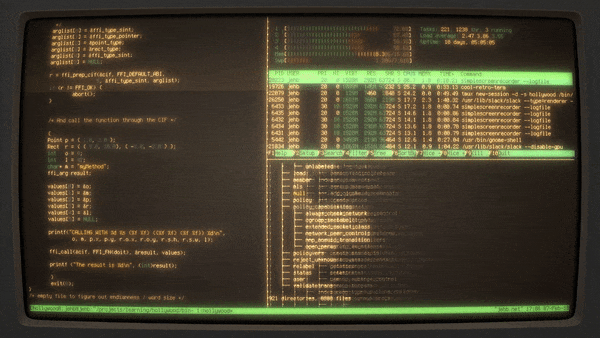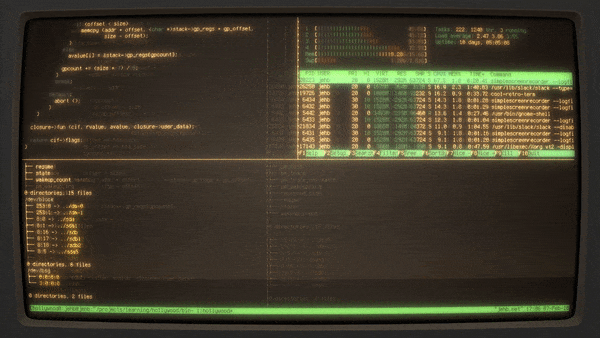
Hack Like a Pro: How to Remotely Grab a Screenshot of Someone's Compromised Computer « Null Byte :: WonderHowTo
Por um escritor misterioso
Descrição

Coding academy 2015 by Joao Ricardo Oliveira - Issuu

HACKER SUMMER CAMP 2023 GUIDES — Part One: Surviving Las Vegas & Virtually Anywhere, by DCG 201

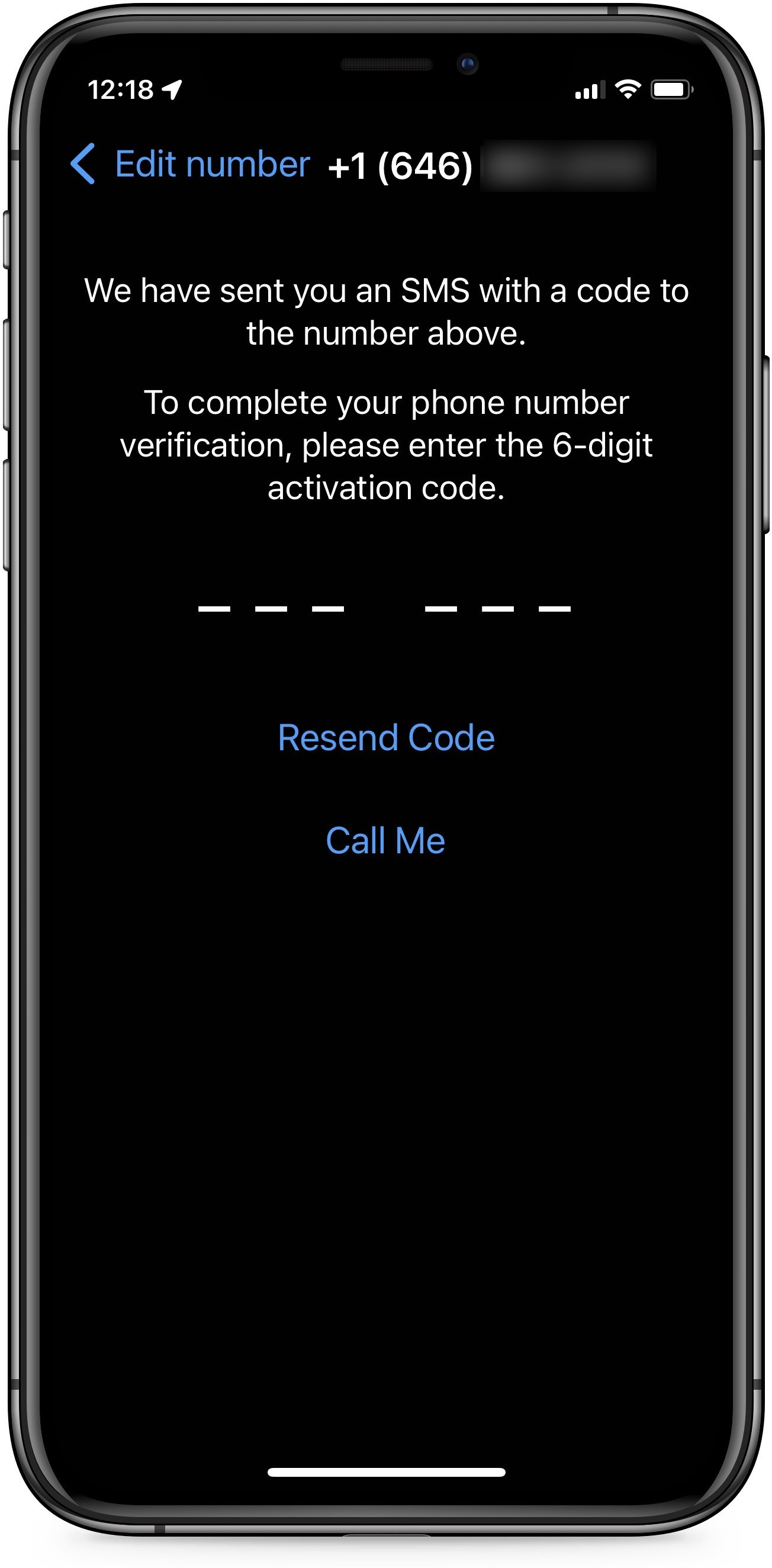
How to Take Screenshots in Windows 10 « Windows Tips :: Gadget Hacks
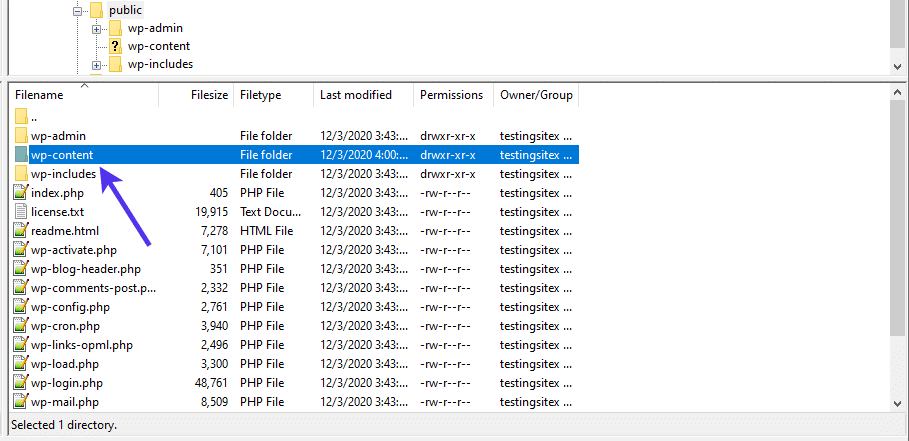
A Comprehensive Guide on WordPress Files and How to Use Them

Web Cracking, PDF, Proxy Server
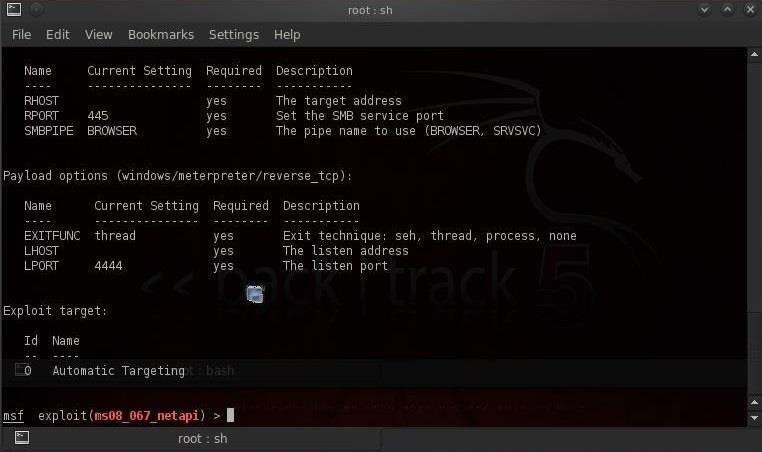
Hack Like a Pro: How to Remotely Grab Encrypted Passwords from a Compromised Computer « Null Byte :: WonderHowTo
The Top 10 Things to Do After Installing Kali Linux on Your Computer [Tutorial]

The hackers manual 2015 revised edition by Gerson Villa Gonzalez - Issuu

How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux

The Best GPUs for Deep Learning in 2023 — An In-depth Analysis

NetCliff Inc.

Best 20 Hacking Tutorials, PDF, Web Application
How to Manage Stored Passwords So You Don't Get Hacked « Digiwonk :: Gadget Hacks
de
por adulto (o preço varia de acordo com o tamanho do grupo)