Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog
Malware analysis lockysample.bin.zip Malicious activity

Unveiling activities of Tropic Trooper 2023 deep analysis of Xiangoop Loader and EntryShell payload

A basic malware analysis method - ScienceDirect

TryHackMe Hacktivities
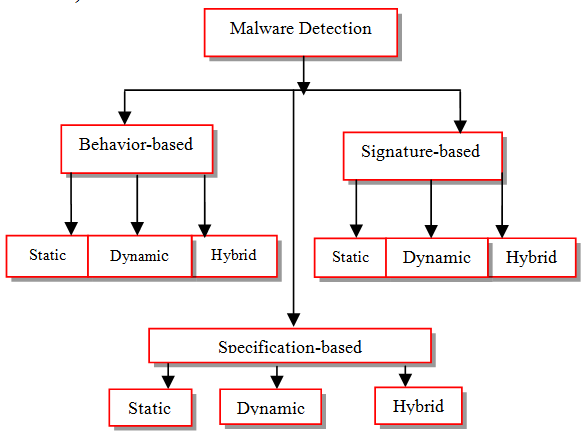
Organization of malware detection techniques (Elhadi et al., 2015)

Dynamic malware analysis [34]

What is Malware? Definition, Types, Prevention - TechTarget

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
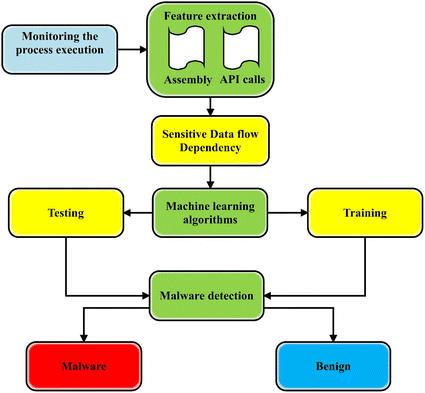
A state-of-the-art survey of malware detection approaches using data mining techniques, Human-centric Computing and Information Sciences

Remediation and Malware Detection Overview

A classification of malware detection techniques.

Malware Analysis: Steps & Examples - CrowdStrike

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber
de
por adulto (o preço varia de acordo com o tamanho do grupo)