Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Malware analysis mykey_.rar Malicious activity

Security Orchestration Use Case: Automating Malware Analysis

Malware analysis metasploit.bat Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike
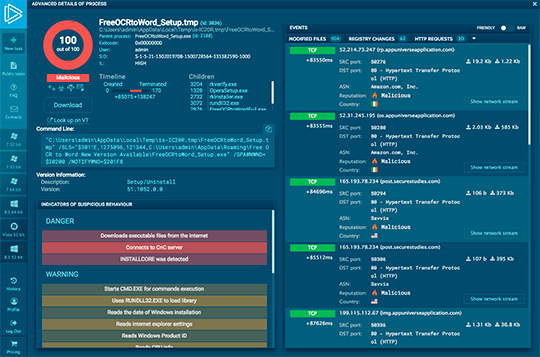
Interactive Online Malware Sandbox
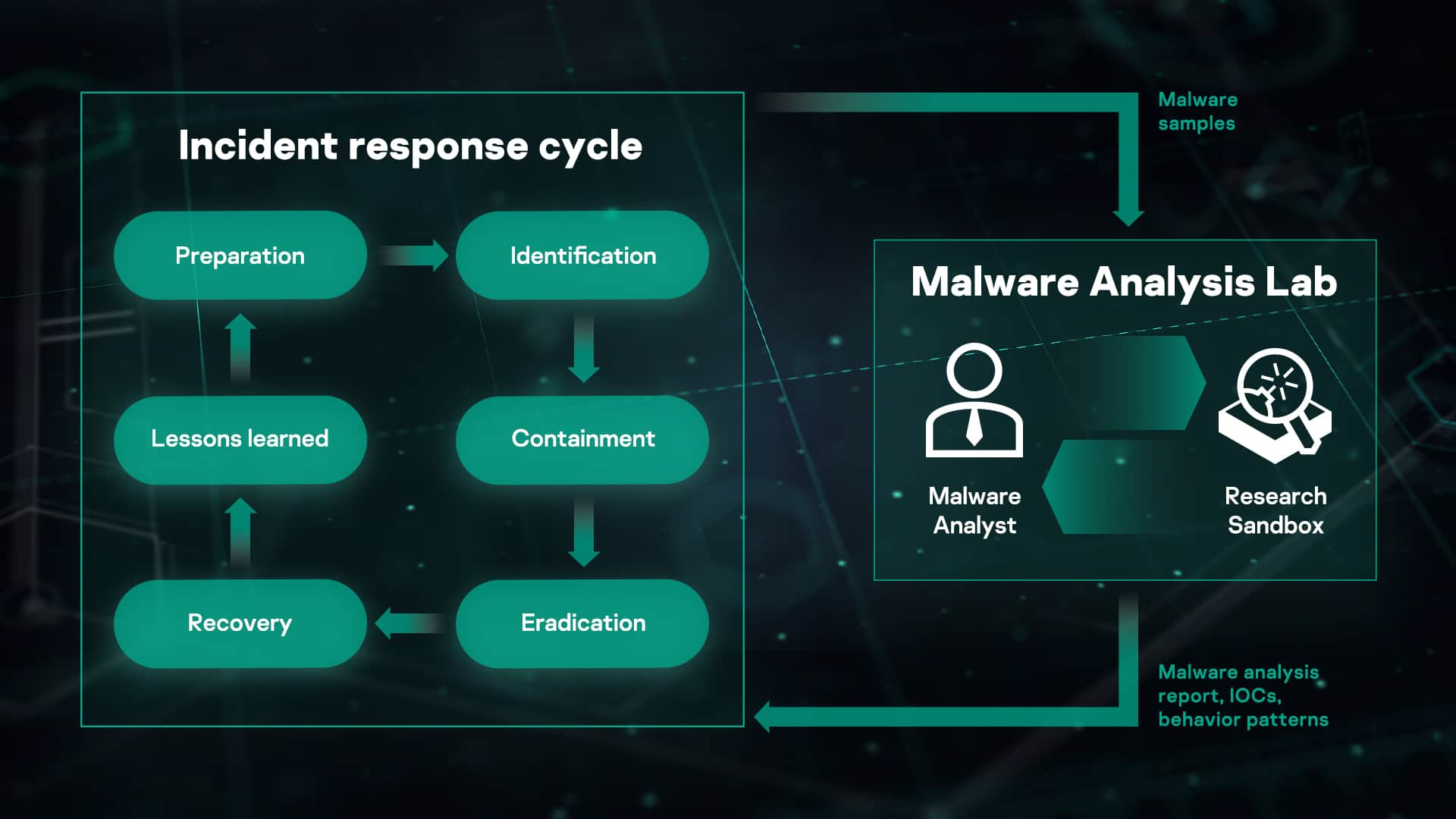
Advanced Automated Malware Analysis – Kaspersky Research Sandbox

The latest malicious activity and how to deal with it

Intro to Malware Analysis: What It Is & How It Works - InfoSec

How to build a malware analysis sandbox with Elastic Security

Malware Analysis: Steps & Examples - CrowdStrike

Endpoint Detection and Response, Free - What is EDR Security?

PROUD-MAL: static analysis-based progressive framework for deep
Download Free Antivirus Software

What to Include in a Malware Analysis Report

Robust Malware Detection Models: Learning From Adversarial Attacks
de
por adulto (o preço varia de acordo com o tamanho do grupo)