Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Descrição
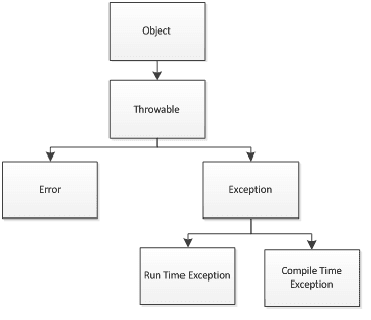
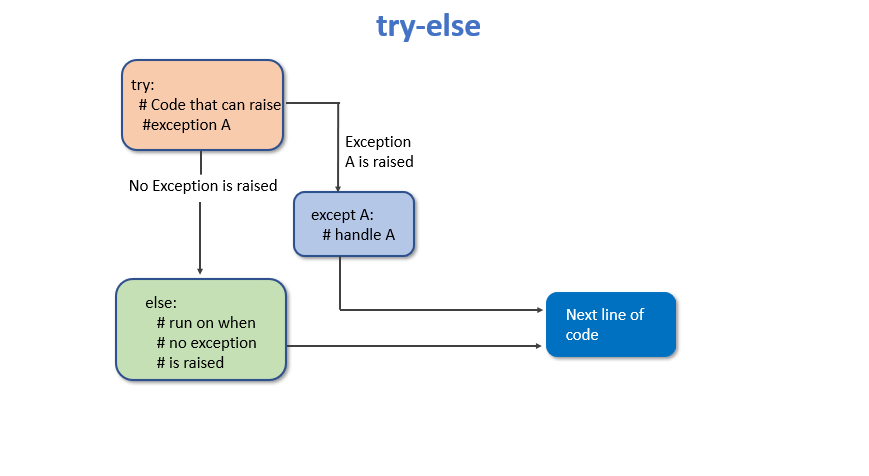
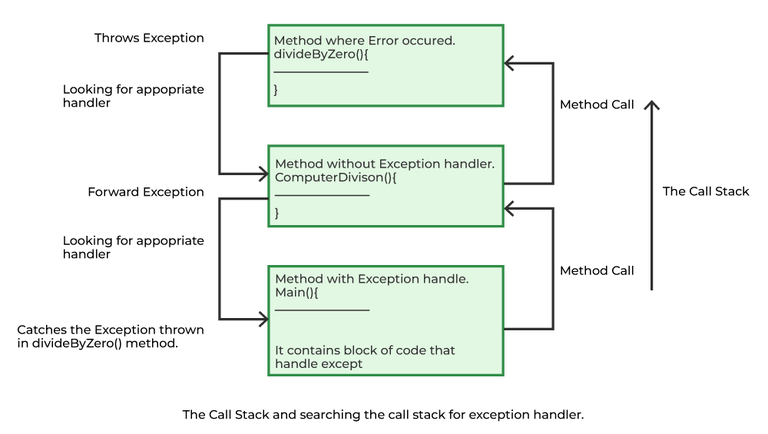
In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

CVE-2021-31956 Exploiting the Windows Kernel (NTFS with WNF

GitHub Actions Security Best Practices [cheat sheet included]

The Architecture of Uber's API gateway
Log4Shell Zero-Day Vulnerability - CVE-2021-44228
Mitigating Abuse of Android Application Permissions and Special

PowerShell Best Practices for Preventing Abuse - Cyber Gladius
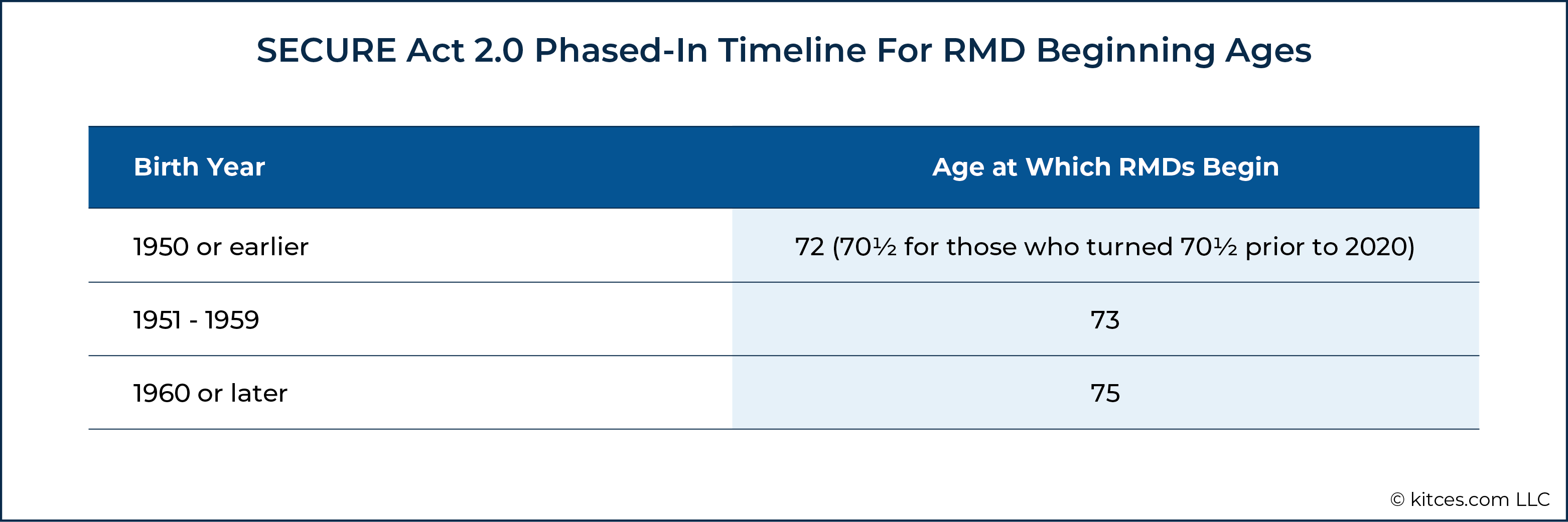
Secure Act 2.0: Detailed Breakdown Of Key Tax Opportunities

How to Prevent and Deal With Referral Fraud and Abuse

Exploiting OGNL Injection in Apache Struts

An Overview of MS-RPC and Its Security Mechanisms
de
por adulto (o preço varia de acordo com o tamanho do grupo)